Cryptocurrency’s popularity has been accompanied by a surge in scams, raising significant concerns in finance. Detecting and staying safe from these scams is crucial for financial protection and personal data security, alongside overall credibility and growth of the crypto ecosystem.
There are many tools and practices that you can employ to keep your wallets safe from hacks and unauthorized third-party access, including revoking and auditing with apps like Revoke, Unicrypt, Ave, and Rugdoc.
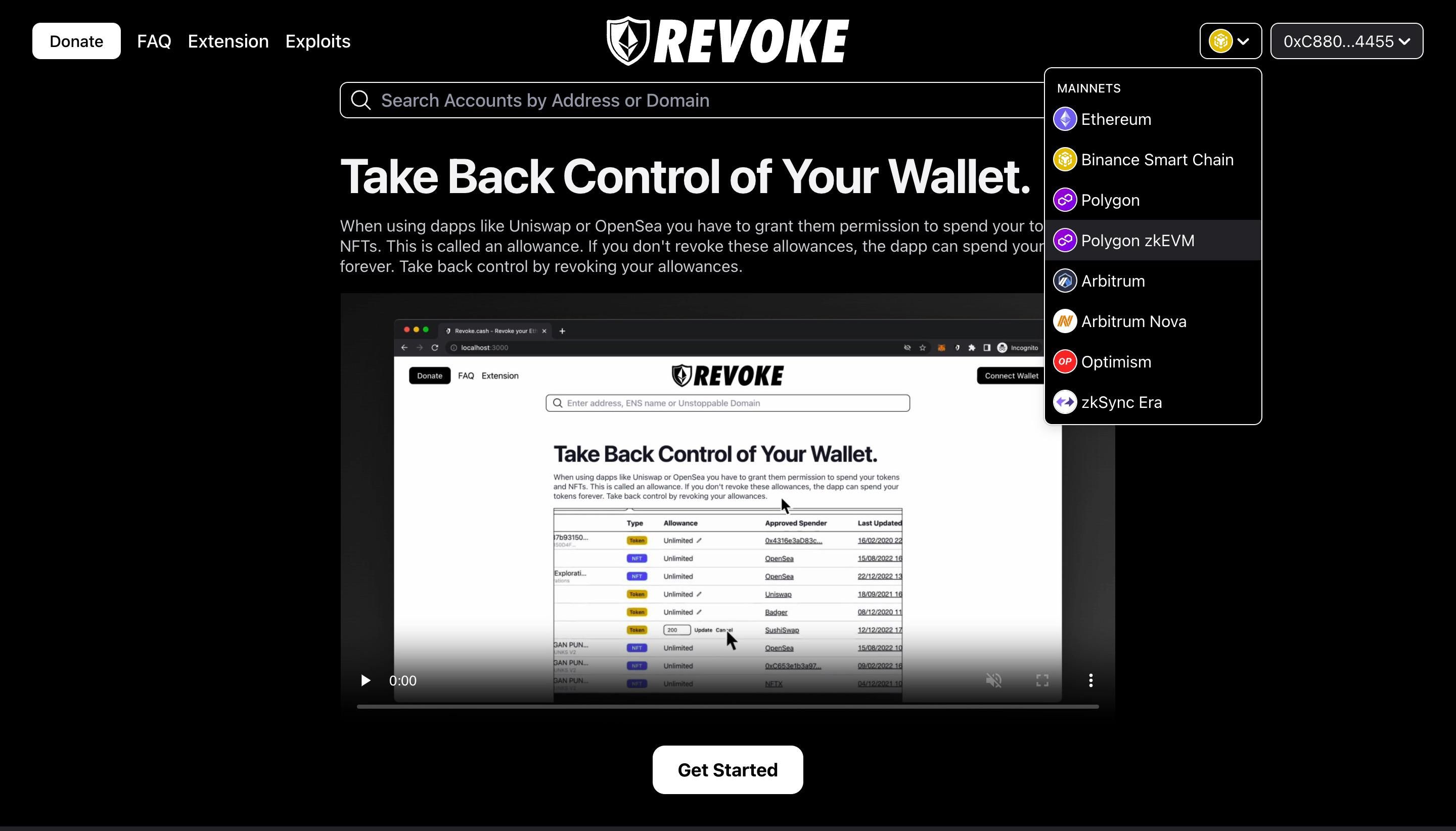
1. Revoke.cash for Revoking Smart Contracts
Revoke.cash is a tool that helps you revoke token allowances from smart contracts.
Token allowances are permissions you give a smart contract to spend a certain amount of tokens from your wallet. Token allowances are often necessary when interacting with a smart contract, including swapping or staking tokens on decentralized exchanges. However, token allowances can also be a security risk. If malicious actors access your wallet, they could use your token allowances to drain your funds.
Revoke.cash connects to your Ethereum wallet and scans your wallet for all the token allowances you have granted to smart contracts. Then you can view a list of all your token allowances and revoke allowances you don’t need.
By using Revoke, you can increase your wallet and fund security. Since Revoke.cash is available on multiple EVM chains, including Binance chain, Polygon, Polygon zkEVM, Arbitrum, Arbitrum Nova, Optimism, and zkSync Era, you can ensure wallet safety as you navigate the multi-chain crypto ecosystem.
Be careful about which contracts you grant token allowances and ensure you use Revoke.cash regularly to avoid loss of funds.
2. UNCX Network for Checking Liquidity Status
UNCX Network is a decentralized platform allowing projects to lock their liquidity tokens, making it more difficult for projects to rug pull or cart away with investors’ funds.
Liquidity is essential in the crypto market. With liquidity, buying and selling assets will be easier, leading to price volatility and market instability. UNCX Network helps to ensure liquidity in the crypto market by providing a way for projects to lock their liquidity tokens.
UNCX Network uses smart contracts to lock liquidity tokens. Thus, the liquidity tokens are held securely and transparently, and projects cannot withdraw without investors’ consent.
When projects want to lock liquidity tokens on UNCX Network, they must create a liquidity pool by depositing equal amounts of the project’s token and a stablecoin, such as USDT or DAI. Then the project must create a liquidity locker by deploying a smart contract that locks the liquidity tokens in the pool.
The liquidity locker is publicly available, meaning anyone can verify the liquidity tokens lock status. This makes it more difficult for projects to rug pull since they need to control the liquidity pool and locker to withdraw the liquidity tokens.
You can use UNCX Network to detect and avoid scam projects by checking the liquidity status of a project before investing. Investing in projects with locked liquidity is safer since they’re less likely to be scams.
To check the liquidity status of a project on UNCX Network, visit the UNCX Network website and enter the project’s address. The website will then display the project’s liquidity status and other information about the project.
3. Token Sniffer for Token Auditing
Token Sniffer is a free online tool for identifying fraudulent tokens and scams. Token Sniffer identifies fraudulent tokens and scams by analyzing the smart contract code of a token while searching for potential security vulnerabilities. Token Sniffer is a valuable tool for investors and developers seeking to protect their projects from scams.
Token Sniffer uses various techniques to identify fraudulent tokens and scams, including smart contract code analysis, checks for known scams, scanning for red flags about the project, etc.
By using Token Sniffer, you can protect yourself from scams, make informed investment decisions and contribute to the security of the blockchain ecosystem.
All you need to do to use Token Sniffer is provide the token’s contract address you want to audit. Token Sniffer will analyze the smart contract code and provide you with a report on the security of the token. The report will include information about the potential security vulnerabilities in the smart contract code and any red flags that suggest the token may be a scam.
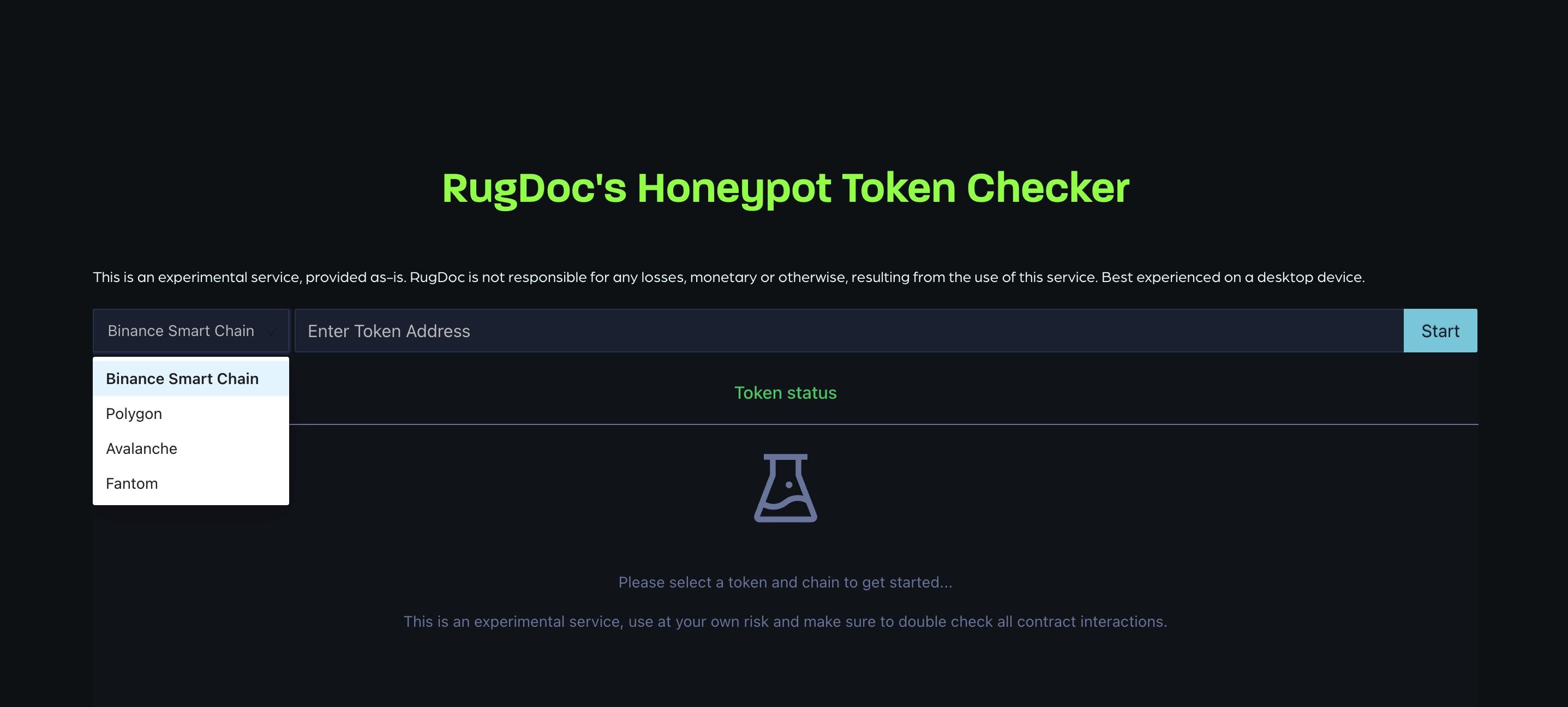
4. Rugdoc Honeypot Token Checker
Honeypot scams are a type of rug pull where the token developers create a smart contract that allows only specified addresses to withdraw tokens; other investors in the token are unable to sell.
The Rugdoc Honeypot Token Checker is a valuable tool for investors to protect themselves from honeypot scams. Rugdoc Honeypot Token Checker is easy to use, accurate, and updated regularly. If you are considering investing in a token, you should use the Rugdoc Honeypot Token Checker to check the token for signs of honeypot scams.
You can use Rugdoc Honeypot Token Checker to check for honeypot scams, check the social media presence for signs of scams, and check the token’s price history for signs of a pump and dump scheme on multiple chains, including BNB Chain, Polygon, Avalanche, and Fantom.
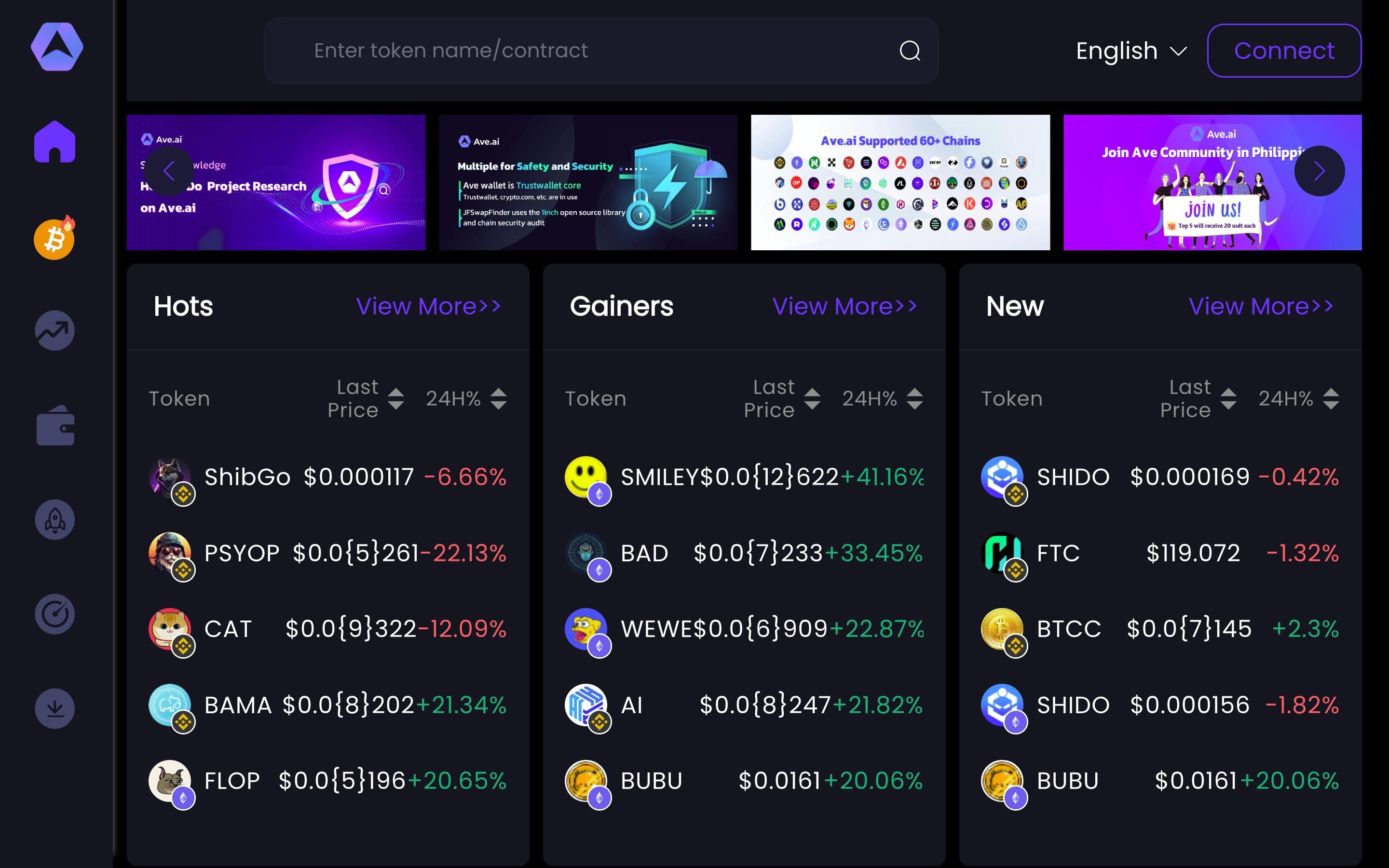
5. Ave.ai for Token Analysis
Ave.ai is a decentralized on-chain data platform aggregating on-chain data from 40+ blockchains. Ave.ai provides users with various tools for token analysis, including K-line data for tokens, the Floor price of NFTs, Statistical data for DeFi, GameFi, Web 3.0, Tokenomics analysis, Social media sentiment analysis, and other features.
You can use Ave.ai’s data to evaluate the legitimacy and potential of tokens by analyzing k-line data to understand the token’s price history and volatility. This can help to gain insight into token-specific data like liquidity and contract status.
By using Ave.ai for your crypto research, you can dive deeper into the smart contract details of a project and check for possible abnormalities.
There Are Other Ways to Secure Your Cryptocurrencies
You can increase your cryptocurrency security by trading on reputable exchanges, storing your cryptocurrencies in multiple cold wallets, using secure internet providers, using two-factor authentication, having multiple passwords, and ensuring that both your internet and crypto browsers are secure.
Credit: Source link