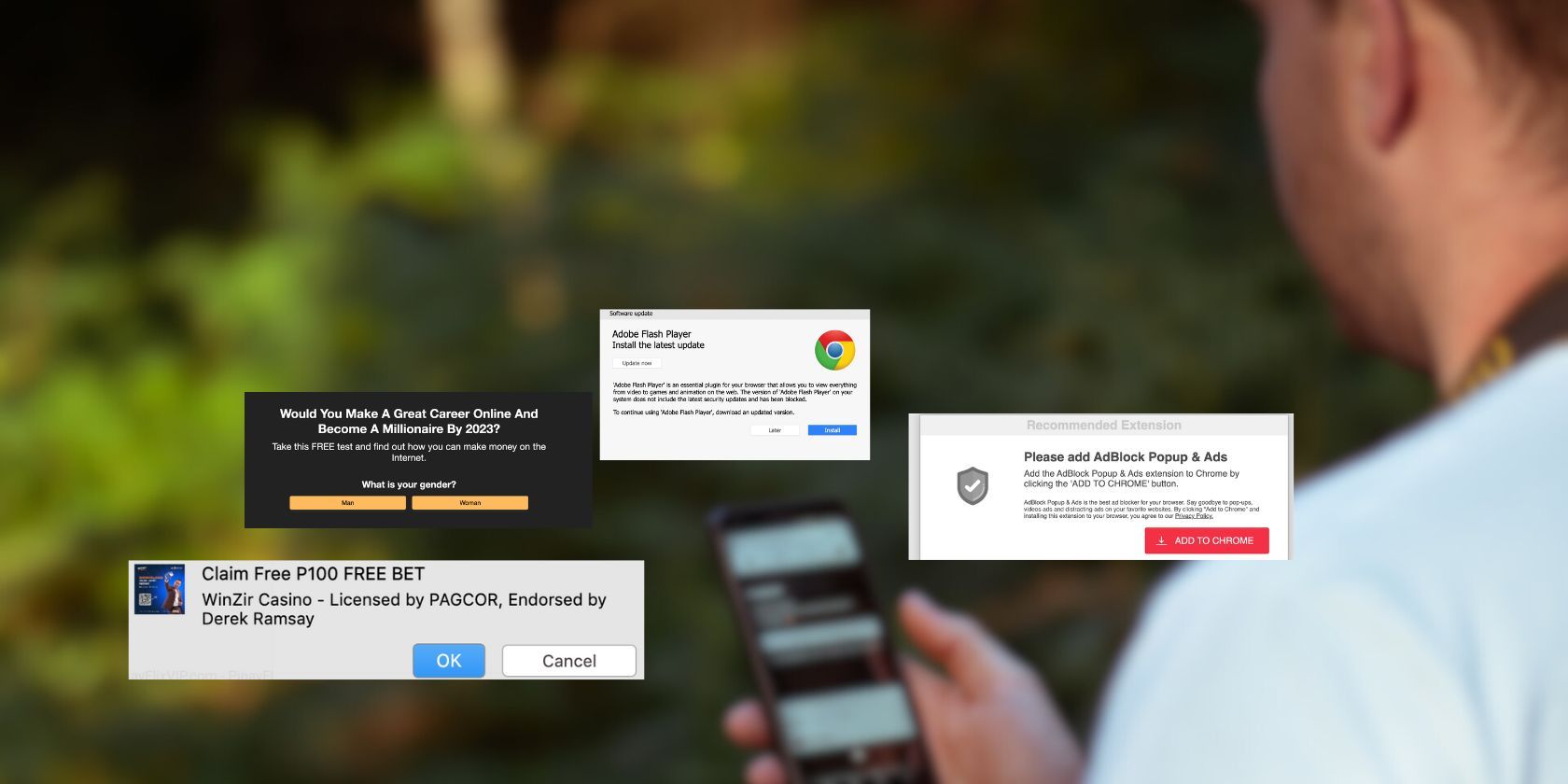
When you think of the typical scam victim, the first thing that may come to mind is a computer-illiterate senior. People assume that being tech-savvy shields you from fraudsters. But in reality, it doesn’t.
Even tech-savvy individuals fall for overused ploys. The FBI receives tens of thousands of online fraud complaints from young adults and teen students. Theoretical knowledge doesn’t combat cybercrime. Here are eight reasons cyberattacks still work on those who are technologically adept.
1. Get-Rich-Quick Schemes Target Young People
Get-rich-quick schemes target young, ambitious individuals. Scammers exploit the latest trends or technologies, find appealing ways to monetize them, then spread their “strategy” online. Yes, some schemes involve legit ventures. But most merely promise absurd profits within short periods in exchange for a “small investment.”
Let’s take cryptocurrency as an example. While there are several legitimate crypto projects, you’ll find just as many self-proclaimed gurus exploiting these tokens. They gain massive traction due to aggressive marketing tactics. Sadly, unsuspecting victims unfamiliar with the common signs of a shady crypto platform take the bait.
Note that get-rich-quick schemes come in many forms, not just crypto projects. Scammers will always keep developing new schemes. To avoid getting roped into them, extensively research your potential ventures. Never invest in technologies you barely understand.
2. Education Makes Users Overconfident
Ironically, individuals who wholly understand cybersecurity and fraud prevention are less vigilant than non-tech-savvy ones. Awareness makes them overconfident. They think tech proficiency automatically safeguards them from fraud attacks, but it doesn’t.
Remember: fraudsters are skilled, professional criminals. Even if you know the signs of scams and cyberattacks, sneaky ones could still fall through the cracks. They have endless ways to bypass common defenses.
Don’t get us wrong—you should still study the latest cybersecurity developments and technologies. Just make sure you go beyond theories. Knowing how to apply your learnings will help prevent a broader range of sophisticated attacks.
3. Digital Natives Rely More on Technology
Owning multiple gadgets has become the norm. The Pew Research Center reports that a typical adult between 18 and 29 owns four devices, including tablets, smartphones, laptops, and gaming consoles. They switch between them throughout the day.
You can own several gadgets, but you should learn to manage them properly. They’re all potential entry points for hackers. Compromising even one could spell disaster for your synced software programs and hardware devices.
4. Chronically Online Users Engage in More Internet Activities
Technologically adept individuals are chronically online. Statista reports that internet users worldwide spent an average of six hours and 35 minutes online daily during the fourth quarter of 2022.
And this figure is the median average. Input from those who barely use the internet tanked the overall results. Many young professionals spend the majority of their day online, especially if they have office jobs.
The internet definitely plays an integral role in modern society. However, spending too much time online, for whatever reason, constantly exposes you to cybersecurity threats, like phishing links and malware. Those who barely go online naturally encounter them far less often.
Tech-dependent individuals have a massive digital footprint. You leave behind “electronic breadcrumbs” as you visit various parts of the internet, from instant messaging apps to news publications. Moreover, some of this data consists of direct identifiers. You’ve probably shared your full name, physical address, or credit card details several times before.
Improve privacy by reducing your online footprint. Since you regularly use the internet for personal and professional purposes, focus on easy, sustainable habits. There’s no need to go off the grid. You can minimize the available information about you by deleting old accounts, setting social networks to private, and running VPNs.
6. Digital Natives Love Using Online Dating Apps
Although any consenting adult can join, dating apps are more popular among young, techie individuals. These services have a slight learning curve, after all. An in-depth knowledge of social network algorithms will help you connect with your ideal partners quickly and efficiently. Meanwhile, those with minimal tech know-how might face issues setting up their profiles.
Despite the popularity of dating apps, they’re also a hotbed of romance scams. And these schemes are becoming more complex. Crooks use AI to create bot accounts, generate realistic photos, and build convincing profiles.
That said, you can still use dating sites. Just be extra cautious—cut ties with anyone who asks for money, offers investments, or aggressively demands suggestive photos.
7. Teens Haven’t Experienced Social Engineering Attacks
Ignorance causes optimism bias. Technologically inclined teens think hacking incidents are distant threats since they’ve never experienced one. As a result, they act carelessly and hastily. These individuals often overlook apparent tricks, like phishing links, infected file attachments, and pop-up viruses.
Don’t underestimate fraudsters. They spend hours daily looking for their targets’ weaknesses—we guarantee they’ll exploit even seemingly minor slip-ups.
As a general rule, view everything with skepticism. Avoid divulging personally identifiable information unless necessary, perform background checks on strangers online, and use social networks sparingly. Address every possible cybersecurity vulnerability. Routine practices feel limiting, but they’re a small price to pay for online privacy.
8. It’s Hard to Incorporate New Habits Into Daily Routines
Like many digital natives, you’ve probably been using technology the same way for years. Relearning even simple safety practices might feel awkward. Take password management as an example. Changing login credentials takes less than five minutes, yet Zippia reports that 65 percent of Americans still recycle passwords.
Granted, forming new habits is hard. But most tech users fail basic behavior-based safety practices because they lack structure. You can’t just suddenly take on new routines. Ease your way into new cybersecurity systems by focusing on one habit at a time. Commit to it every day. You’ll eventually perform security checks without conscious effort through repetition and consistency.
Remember: Complacency Causes Critical Security Errors
Even professionals adept at using modern systems could fall for hacking attacks if they’re careless. Complacency and overconfidence often cause a lapse of judgment. To ensure your safety, faithfully commit to simple yet effective cybersecurity practices. The basics go a long way.
Also, revisit the most common social engineering attacks. Always watch out for red flags. Most cyberattacks only work if they take you by surprise—safeguard yourself by staying informed and cautious.
Credit: Source link