Scammers demanding low in Bitcoin manage to remain under the radar. (Source – Shutterstock)
- Email fraud is on the rise, notably in Asia, where phishing scams target complaint filers.
- Scammers evade detection by making moderate demands from few accounts.
- Barracuda underscores the need for AI security, employee education, and firm security policies to counter scams.
Analyzing the numbers tied to email scammers shows that no part of the world, including Asia, is safe from a recent surge in this type of cybercrime. The past few years have marked a notable surge in email fraud incidents in this part of the world, reflecting a consistent increase in this type of cybercrime.
These unscrupulous individuals take advantage of the simplicity and obscurity of email communication to dupe unsuspecting individuals, leading to substantial financial damage and potential harm to personal lives. The modus operandi of these cybercriminals varies extensively from phishing schemes to advanced fee scams, reflecting a diversity as vast as their potential victims.
As an instance, in 2022, fraudsters have resorted to phishing emails as a means to pry information from those who’ve filed complaints with the Consumers Association of Singapore (Case). They mislead these individuals by directing them to unrelated third-party websites under the guise of providing case updates.
Within these deceptive emails, fraudsters provide victims with bogus ticket numbers related to their disputes or claims. Following this, they guide the recipients to click on a chat icon, which links them to third-party websites, supposedly for the purpose of updates or to receive financial redress.
In line with Barracuda’s findings, email fraudsters who resort to threats of exposing incriminating or unlawful material to squeeze money out of victims generally aim for fewer than 10 work email accounts at a time. This strategy, paired with moderate monetary demands, helps them slip under the radar.
An investigation carried out by researchers at Columbia University, which studied 300,000 emails flagged as blackmail scams over a year in Asia and worldwide by Barracuda’s AI detectors, was designed to expose the financial underpinnings of these extortion emails.
In Barracuda’s latest Threat Spotlight, the research showed that scammers demanding around US$1000 in Bitcoin manage to remain under the radar, circumventing the suspicion of potential victims, security teams, and payment systems.
The nature of extortion attacks involves the threat of exposing sensitive information, such as photos, videos, or details of illegal online activities, unless the victims pay the culprits, typically in a cryptocurrency like Bitcoin.
The well-structured Bitcoin infrastructure facilitates transactions for victims and allows culprits to further mask their activities using ‘mixers.’ These services mix and split Bitcoin from various wallets, blurring transaction histories. Furthermore, thanks to the public nature of the blockchain, it is straightforward to check whether a victim has made a payment, circumventing the problems of traditional transactions.
Are scammers demanding big numbers?
The researchers at Columbia classified the extortion emails based on the Bitcoin wallet addresses within them. The team found 3,000 unique Bitcoin wallet addresses, with 100 of them appearing in 80% of the emails. This implies that a relatively small group of culprits were behind most of the extortion emails.
The team further scrutinized the sender email fields for each extortion email. They discovered that 97% of sender accounts dispatched fewer than 10 extortion emails each, with 90% of the attacks demanding less than US$2,000 in Bitcoin.
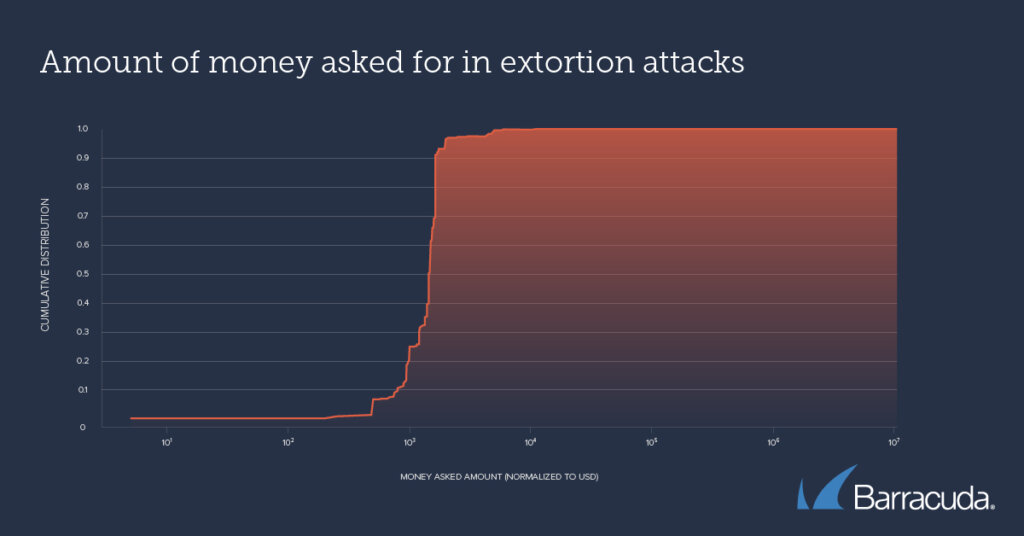
Amount of money asked for in extortion attacks (Source – Barracuda)
Asaf Cidon, Associate Professor of Electrical Engineering at Columbia University, noted that their analysis indicates extortion scams are orchestrated by a small group of individuals, each conducting numerous small-scale attacks with moderate demands.
Cidon remarked, “These relatively modest sums make it likelier the targets will cooperate with the extortion, and the relatively small number of emails per sender make it easier for attackers to evade detection by traditional security technologies and anti-fraud measures at payment providers and avoid arousing the attention of law enforcement and the media – which would alert potential victims to the scam.”
Mark Lukie, Director of Solution Architects (APAC) at Barracuda, stressed the importance of taking extortion attacks seriously, especially when targeting individuals through their work email accounts.
Lukie queried, “How did the attacker get hold of the account details, for example – were they exposed or stolen at some point? Or does it mean that the recipient has used their work account and device for inappropriate activity such as visiting questionable websites? Both scenarios have security implications for the company – and for the target. This can be embarrassing and distressing and can potentially make it more likely a victim will pay.”
Barracuda recommends certain critical steps that security teams can implement to shield employees and the organization from extortion scams. These measures include investing in AI-powered email security that can detect and block such emails, and preventing attackers from hijacking accounts. It’s equally important to train employees and enforce security policies that discourage using work email for accessing third-party sites or storing sensitive personal content on work devices, while also providing a secure and confidential way to report an incident.
Credit: Source link