As the popularity of cryptocurrency skyrockets, crypto scammers are seizing opportunities to exploit unsuspecting users. One such method involves the malicious use of Google Ads to facilitate phishing attacks or hacking AT&T email accounts.
Scammers purchase ads that top search results, luring victims to counterfeit websites where their sensitive information and funds are stolen. With millions of dollars lost, there is a pressing need for Google to enforce stricter ad screening measures.
The Anatomy of a Google Ads Phishing Scam
Scammers first create fake websites that closely resemble legitimate platforms to execute these schemes. These websites may use similar logos, designs, and domain names, making it challenging for users to differentiate between genuine and fraudulent sites.
Crypto scammers also employ social engineering tactics, such as creating a sense of urgency or offering lucrative incentives, to convince users to divulge their personal information.
Next, cybercriminals invest in Google Ads to promote their fraudulent sites, ensuring they appear prominently in search results. These ads are designed to attract users interested in cryptocurrencies by utilizing relevant keywords and targeting specific demographics.
Unsuspecting users click on these ads and, believing they are on authentic websites, enter sensitive information that the crypto scammers can then exploit.
The Impact of Google Ads Phishing
Phishing scams facilitated by Google Ads have resulted in the theft of millions of dollars, damaging the reputation of legitimate businesses and eroding user trust.
The prevalence of these scams highlights the necessity for Google to implement more rigorous ad screening processes to protect users and maintain the integrity of its platform.
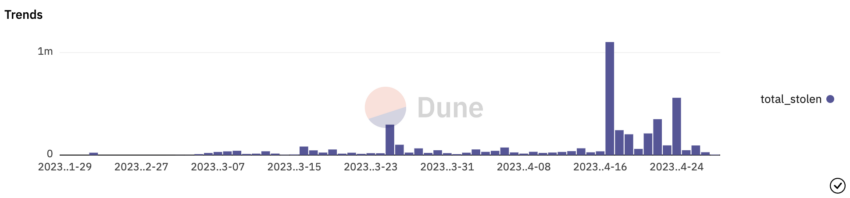
Moreover, these phishing attacks not only lead to financial losses for the victims but also contribute to the negative perception of the cryptocurrency industry as a whole. The ongoing occurrence of scams can deter potential investors and hinder the mainstream adoption of cryptocurrencies.
AT&T Email Accounts: A Gateway to Crypto Theft
In a separate and equally nefarious operation, crypto scammers are exploiting AT&T email accounts to steal cryptocurrency.
By identifying security weaknesses in these accounts, cybercriminals gain unauthorized access, change passwords, and use compromised accounts to reset passwords on cryptocurrency exchanges. Consequently, victims are locked out of their accounts, and their digital assets are stolen.
These incidents have tarnished AT&T’s reputation as a secure email service provider and have led to calls for improved security measures.
The AT&T Email Hacking Process
The process of hacking AT&T email accounts begins with the identification of vulnerable accounts. Cybercriminals may utilize various methods to achieve this, such as exploiting leaked databases containing user credentials, brute force attacks, or phishing emails designed to deceive users into revealing their passwords.
Once they gain unauthorized access, the crypto scammers change the account passwords, effectively hijacking them. The compromised accounts are then used to reset passwords on cryptocurrency exchanges, granting the hackers control over the victims’ digital assets.
In some cases, the attackers may also use the stolen email accounts to launch further phishing attacks, perpetuating the cycle of fraud and theft.
The Consequences of AT&T Email Hacks
The hacks targeting AT&T email accounts have not only resulted in the loss of millions in cryptocurrency but have also damaged the company’s reputation as a secure email service provider.
As the number of incidents continues to rise, AT&T must take decisive action to enhance its security measures and protect its users from further breaches.
In addition to financial losses, victims of these hacks may also suffer from identity theft and other privacy violations. The long-term consequences of these breaches can include damaged credit scores, difficulties in obtaining loans or credit, and ongoing monitoring of personal information to prevent further exploitation.
Preventing Crypto Scams and Strengthening Security Measures
To combat these growing threats, collaboration among industry stakeholders is vital. Google must implement more robust ad screening processes, while AT&T should enhance its email security measures.
Users must also remain vigilant and adopt best practices to safeguard their digital assets.
User Best Practices for Online Security
- Always verify website URLs before entering personal information. Double-check the domain name and look for signs of legitimacy, such as SSL certificates and secure connection indicators.
- Use strong, unique passwords and enable two-factor authentication for added security. Avoid using easily guessable information, and consider using a password manager to help manage multiple accounts.
- Exercise caution when receiving unsolicited emails and avoid clicking on unexpected password reset requests. Be wary of emails containing typos, grammatical errors, or suspicious links, as these may indicate phishing attempts.
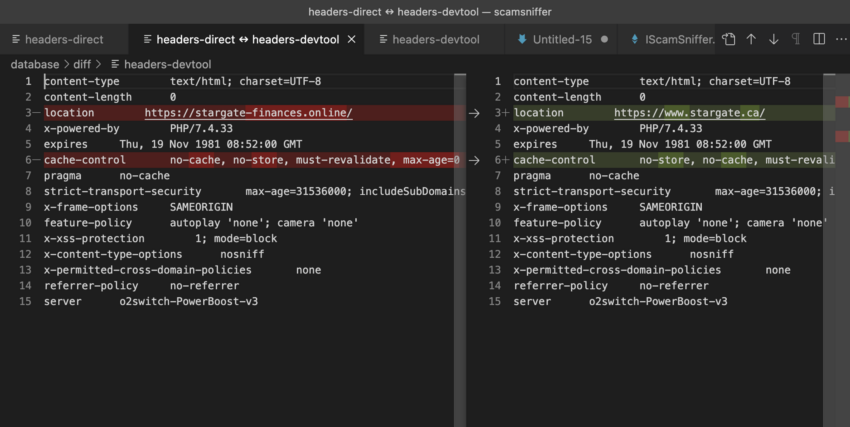
The Role of Companies in Enhancing Online Security
Companies like Google and AT&T must assume responsibility for securing their platforms to protect users from crypto scams and hacks. Google can improve its ad screening process by:
- Implementing stricter policies for ads promoting financial services and cryptocurrency platforms. This could include requiring advertisers to undergo identity verification and demonstrate regulatory compliance.
- Employing machine learning algorithms to identify and block fraudulent ads. Advanced technology can detect patterns indicative of crypto scams, allowing Google to take preemptive action against malicious ads.
- Collaborating with the crypto community to build a database of known scam websites. The industry can more effectively combat fraudulent actors and protect users from potential harm by pooling resources and information.
AT&T, on the other hand, can enhance its email security by:
- Implementing multi-factor authentication (MFA) as a default setting for all email accounts. This additional layer of security can help prevent unauthorized access, even if a hacker manages to obtain a user’s password.
- Regularly updating security protocols and software to address vulnerabilities. By promptly staying informed about emerging threats and patching security flaws, AT&T can minimize the risk of successful cyberattacks.
- Offering educational resources to users on how to recognize and avoid phishing attempts. By providing guidance and support, AT&T can empower its users to take proactive steps to protect their accounts and personal information.
The Community’s Role in Combating Crypto Scammers
The cryptocurrency community is also responsible for joining forces in tackling scams and hacks. Collaboration can be achieved through:
- Reporting phishing websites and suspicious emails to relevant authorities and platforms. The community can help others avoid falling victim to scams by sharing information about potential threats.
- Sharing information about known scams and hackers within the community. Publicizing details about fraudulent actors can raise awareness and prompt action from industry stakeholders.
- Developing decentralized solutions for improved user security and privacy. By harnessing the power of blockchain technology, the crypto community can create innovative solutions to enhance trust and security within the ecosystem.
A Call to Action for a Safer Crypto Ecosystem
As the cryptocurrency market continues to expand, effective security measures and collaboration among stakeholders are crucial. By working together, companies like Google and AT&T and the broader crypto community can create a safer environment for users, reducing the impact of scams and hacks.
With the implementation of more robust security measures and increased user awareness, the cryptocurrency ecosystem can become a safer space.
The combined efforts of companies, communities, and individuals will prove critical in combating scams and hacks, ultimately fostering a more secure and trustworthy environment for all.
Disclaimer
Following the Trust Project guidelines, this feature article presents opinions and perspectives from industry experts or individuals. BeInCrypto is dedicated to transparent reporting, but the views expressed in this article do not necessarily reflect those of BeInCrypto or its staff. Readers should verify information independently and consult with a professional before making decisions based on this content.
Credit: Source link








%20(1).png)